aws
Pulumi: The Real Infrastructure as Code
Over the years, several IaC tools have emerged, each with its own strengths and weaknesses. Among these, Pulumi has gained significant attention for its unique approach and capabilities.
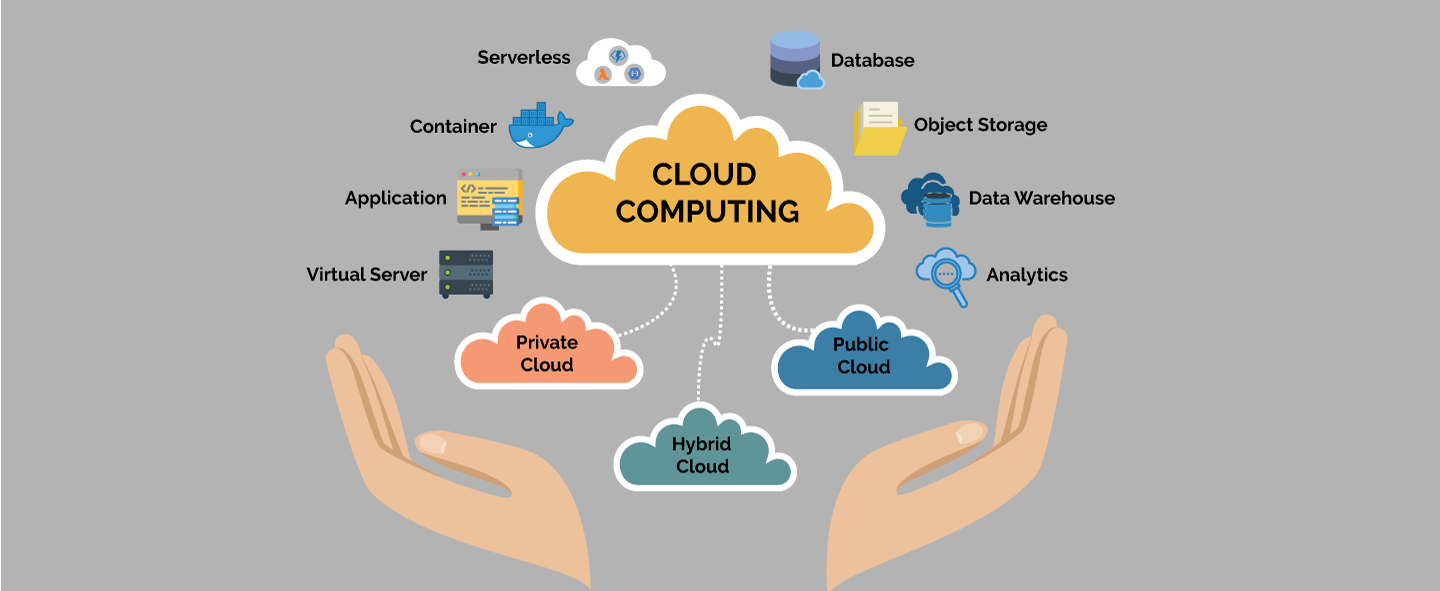
Cloud Computing: The Fundamental
In today's digital age, cloud computing has become a critical component of our daily lives, powering everything from social media to online banking.
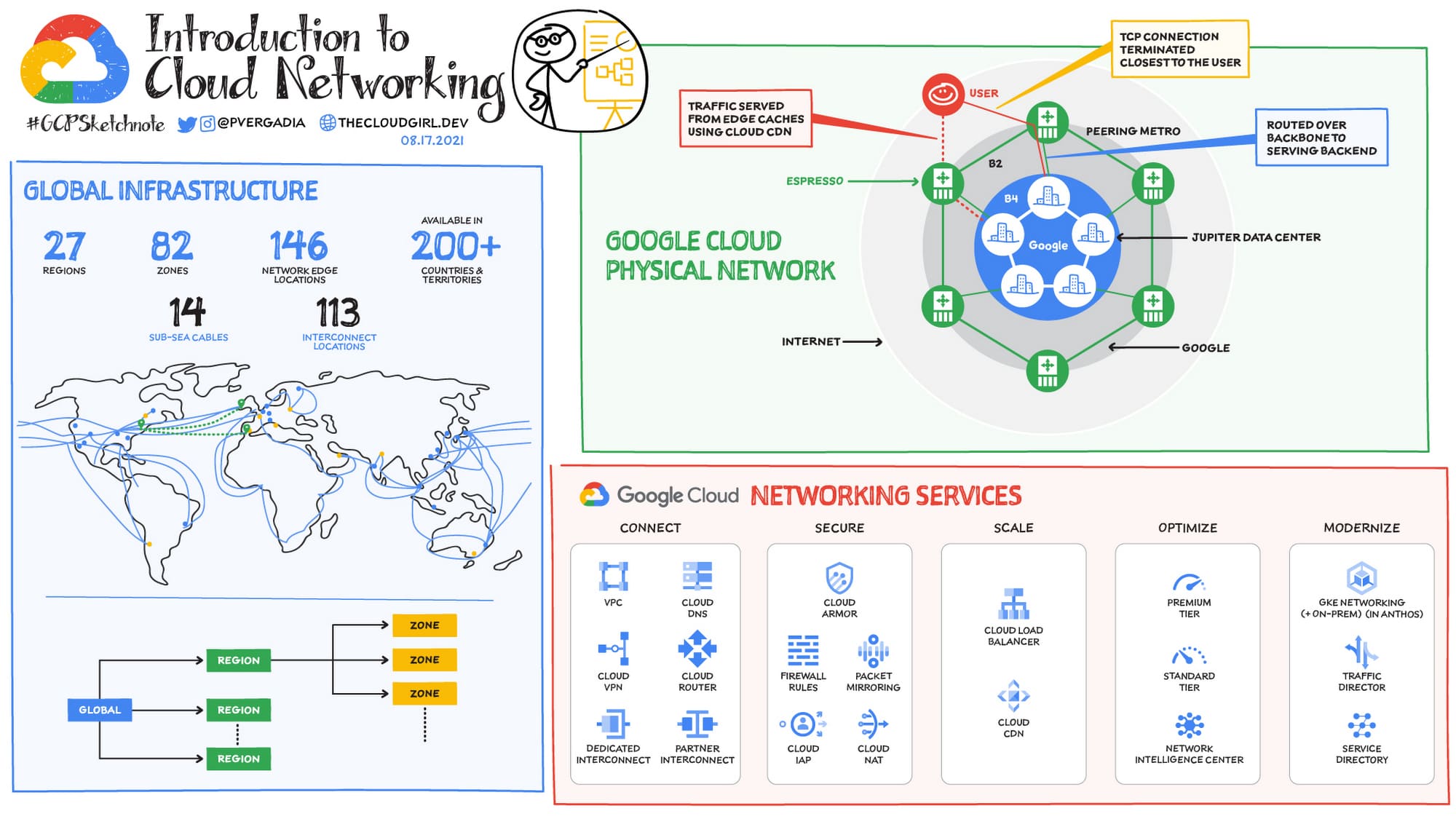
An Introduction to Google Cloud Platform Networking
Google Cloud Platform (GCP) offers a robust and efficient environment for deploying and managing cloud applications. A key aspect of GCP is its networking capabilities, which are designed to be secure, scalable, and high-performing.
Why choose Google Cloud Platform (GCP)?
Per 25 April 2023, Google Cloud finally make profits for the first time. Google has been investing heavily in its cloud-computing division to compete with Amazon and Microsoft, and those significant investments are now yielding profits.
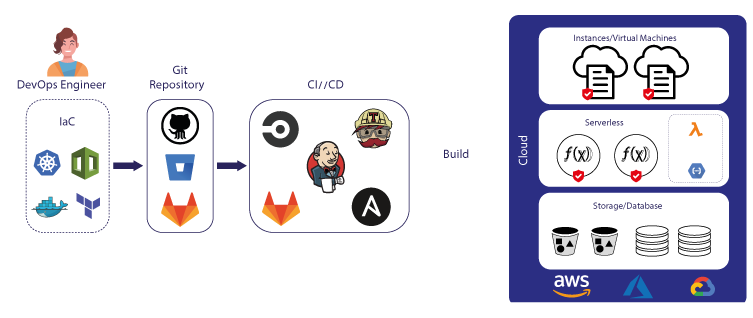
What is Infrastructure as Code and why you should care about it?
Infrastructure as Code (IaC) is an approach to managing and provisioning IT infrastructure through the use of machine-readable definition files, rather than manual hardware configuration or interactive configuration tools.
Free Consultation!
Get a free consultation to assess your business needs and discover tailored solutions. Leverage expert insights to optimize your strategy, streamline operations, and achieve your goals.