LXD & LXC: Linux Container to rule them all
In recent years, containerization has revolutionized the way software is developed, deployed, and managed. Containers offer lightweight, isolated environments that enable applications to run consistently across various environments, making them an attractive alternative to traditional VM

Introduction
In recent years, containerization has revolutionized the way software is developed, deployed, and managed. Containers offer lightweight, isolated environments that enable applications to run consistently across various environments, making them an attractive alternative to traditional virtual machines (VMs). This shift has led to the rise of several container technologies, including Docker, LXC, and LXD. LXC (Linux Containers) and LXD (Linux Container Daemon) stand out for their approach to system containers, providing robust solutions for running full Linux distributions within isolated environments.
Understanding LXC and LXD
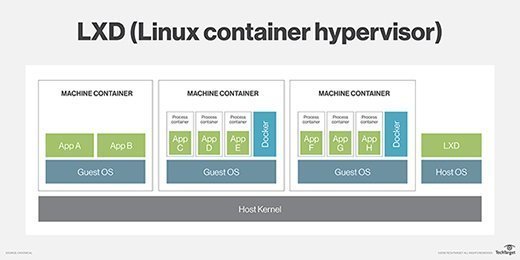
LXC (Linux Containers)
LXC is a form of operating system-level virtualization that allows multiple isolated Linux systems, known as containers, to run on a single host. Unlike traditional virtualization methods, which virtualize the hardware, LXC leverages the host's operating system to create containers that share the host's kernel but remain isolated from each other. This makes LXC containers lightweight and efficient, ideal for scenarios requiring high performance and resource optimization.
LXD (Linux Container Daemon)
LXD builds on top of LXC, offering a more user-friendly and feature-rich experience. LXD acts as a system container manager that simplifies container management through a REST API, command-line tools, and other enhancements. While LXC focuses on providing the basic tools for container creation and management, LXD introduces additional functionalities such as image management, network management, and a client-server model, making it easier to deploy and orchestrate containers at scale.
Historical Background
The concept of containerization dates back several decades, with early implementations aimed at isolating processes and managing resources efficiently. However, the modern container landscape began to take shape with the development of LXC in 2008. LXC emerged as a robust solution for creating lightweight containers using Linux kernel features like namespaces, control groups (cgroups), and chroot.

As container adoption grew, so did the need for more advanced management capabilities. This led to the development of LXD by Canonical in 2015. LXD was designed to address the limitations of LXC, providing a more intuitive and powerful container management experience. With LXD, users could easily create, manage, and monitor containers through a simple command-line interface or REST API, significantly enhancing the usability and scalability of Linux containers.
Motivation for Creating LXC and LXD
The primary motivation behind the creation of LXC and LXD was to address the inefficiencies of traditional virtualization methods. Virtual machines, while effective for isolating and managing workloads, come with significant performance overhead. Each VM requires a separate operating system instance, consuming considerable CPU, memory, and storage resources. This overhead limits the number of VMs that can run on a single host and affects overall system performance.
In contrast, LXC containers share the host's kernel, reducing the need for redundant OS instances and minimizing resource consumption. This makes LXC containers more lightweight and efficient, allowing for higher density and better performance. Additionally, LXC's ability to provide isolated environments without the overhead of full VMs made it an attractive solution for various use cases, from development and testing to production deployments.
Despite these advantages, managing LXC containers at scale posed challenges, especially in complex environments. This led to the development of LXD, which introduced enhanced management capabilities and simplified container orchestration. LXD's user-friendly interface and additional features addressed the needs of modern container deployments, making it easier for users to leverage the benefits of LXC while overcoming its limitations.
Core Concepts
LXC and LXD rely on several core concepts and architectural components to provide efficient and isolated container environments.
Namespaces
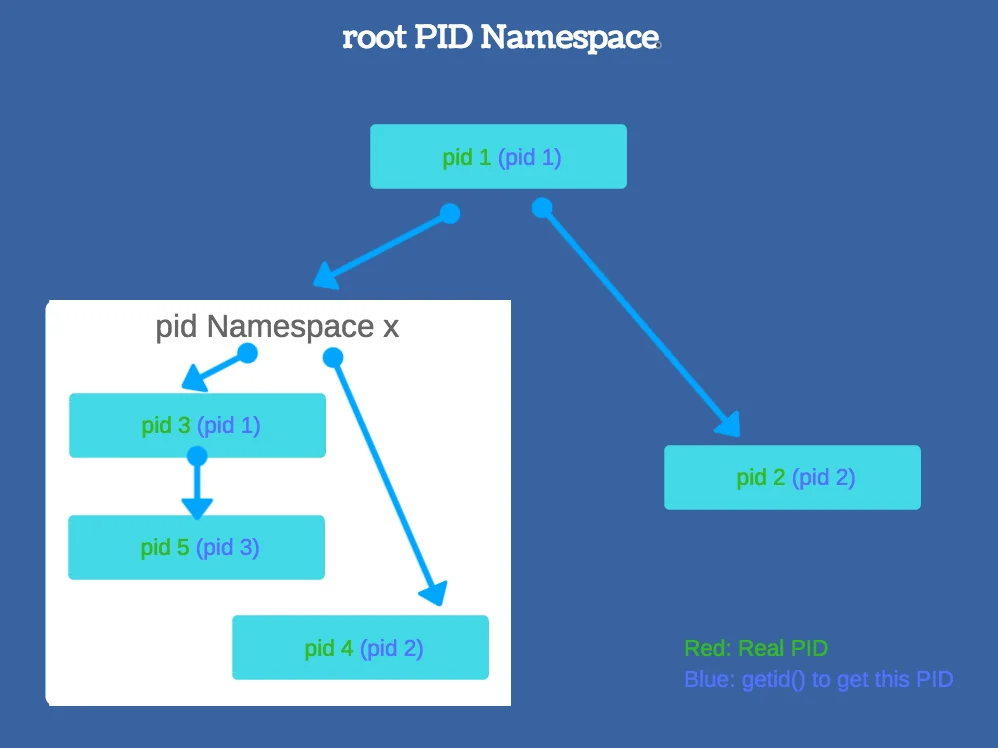
Namespaces are a fundamental feature in Linux that enable isolation of system resources. By using namespaces, LXC containers can have their own isolated instances of process IDs, user IDs, file names, network interfaces, and more. This ensures that processes within a container are separated from those in other containers and the host system. For example, a container can have its own network stack, allowing it to have unique IP addresses and network configurations, completely isolated from the host and other containers.
Control Groups (cgroups)
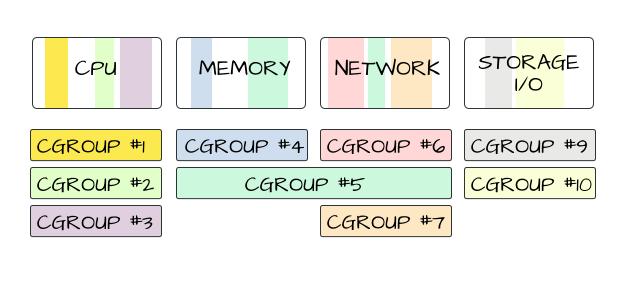
This is another crucial component, allowing the kernel to allocate and limit resources such as CPU, memory, and disk I/O to containers. Cgroups provide fine-grained control over resource usage, ensuring that containers do not interfere with each other's performance and maintaining overall system stability. For instance, cgroups can be used to set limits on the amount of CPU time or memory a container can use, preventing a single container from consuming all the host's resources.
Chroot
It is a technique that changes the root directory for the current running process and its children. This creates a contained filesystem environment, further isolating containers from the host system. While not a comprehensive isolation mechanism, chroot adds an additional layer of security and containment. It ensures that a container's filesystem is separate from the host's filesystem, preventing containers from accessing or modifying files outside their designated environment.
Daemon
It refers to the background process that manages container operations. In the case of LXD, the daemon handles requests for creating, starting, stopping, and deleting containers. It interacts with the underlying LXC tools to perform these operations, providing a seamless management experience. The LXD daemon also manages networking, storage, and other resources, ensuring that containers are efficiently and securely managed.
Images
Images are templates used to create containers. An image includes a minimal filesystem and the necessary configurations to run a container. LXD supports various image types, including custom and pre-built images, making it easy to deploy containers with specific configurations and software stacks. For example, an LXD image might contain a basic Ubuntu operating system, pre-configured with necessary libraries and tools for a particular application.
Profiles
Profiles in LXD are sets of configurations that can be applied to containers. Profiles define various settings such as resource limits, network configurations, and storage options. By using profiles, administrators can standardize container configurations and simplify management. For instance, a profile might specify that all containers using it should have a certain amount of CPU and memory, specific network settings, and mount points for shared storage.
Snapshots
Snapshots are point-in-time copies of containers. They enable users to create backups of container states and easily rollback to previous states if needed. Snapshots are useful for maintaining data integrity and recovering from errors or misconfigurations. For example, before making significant changes to a container, an administrator might create a snapshot, allowing them to revert to the previous state if something goes wrong.
Network Bridges
Network Bridges are link layer devices that forward traffic between network segments. In the context of LXC/LXD, network bridges provide networking capabilities to containers, allowing them to communicate with each other and external networks. LXD offers advanced networking options, including support for various network configurations and virtual networks. This enables containers to have their own network interfaces and IP addresses, and to be part of complex network topologies.
REST API
It is a set of functions that enable interaction with LXD programmatically via HTTP requests. The REST API allows users to automate container management tasks, integrate LXD with other tools and systems, and build custom management solutions. For example, an organization might use the REST API to integrate LXD with their CI/CD pipeline, automating the creation and deployment of containers for testing and production environments.
Client-Server Model
This model in LXD separates the management of containers (server) from the interface used to interact with them (client). This architecture enhances scalability and flexibility, allowing users to manage containers across multiple hosts and environments. The client communicates with the LXD daemon on the server, sending commands and receiving responses. This model enables centralized management of containers, even in distributed environments.
Benefits of Using LXC and LXD
The adoption of LXC and LXD brings numerous benefits, making them an attractive choice for containerization.
- Efficiency and Performance: LXC containers are lightweight and share the host's kernel, resulting in lower resource overhead compared to VMs. This efficiency translates to faster startup times and better utilization of CPU, memory, and storage resources. As a result, more containers can run on a single host, maximizing hardware usage and reducing costs. For example, a development environment with limited resources can support multiple containers running different applications without the need for multiple VMs.
- Scalability: LXD simplifies the management of large-scale container deployments. Its client-server model, REST API, and command-line tools make it easy to orchestrate and manage hundreds or thousands of containers across multiple hosts. This scalability is crucial for modern cloud-native applications and microservices architectures, where containers need to be deployed and managed dynamically. An enterprise can use LXD to manage a fleet of containers running microservices, scaling them up or down based on demand.
- Security and Isolation: LXC and LXD provide strong isolation through namespaces, cgroups, and chroot. This isolation ensures that containers do not interfere with each other or the host system, enhancing security and stability. LXD also includes built-in security features, such as apparmor profiles and secure networking configurations, further strengthening container security. For instance, sensitive applications can run in isolated containers with restricted resource access, reducing the risk of security breaches.
- Flexibility and Versatility: LXC and LXD are versatile and can be used for a wide range of scenarios, from development and testing to production deployments. They support both system containers (full OS instances) and application containers, making them suitable for various use cases. Additionally, LXD's support for custom profiles, snapshots, and network configurations allows users to tailor containers to their specific needs. A developer can use LXC for isolated development environments, while an IT operations team can use LXD for managing production workloads.
Comparison with Docker
While LXC and LXD focus on system containers, Docker is primarily designed for application containers. This fundamental difference leads to several architectural and functional distinctions.
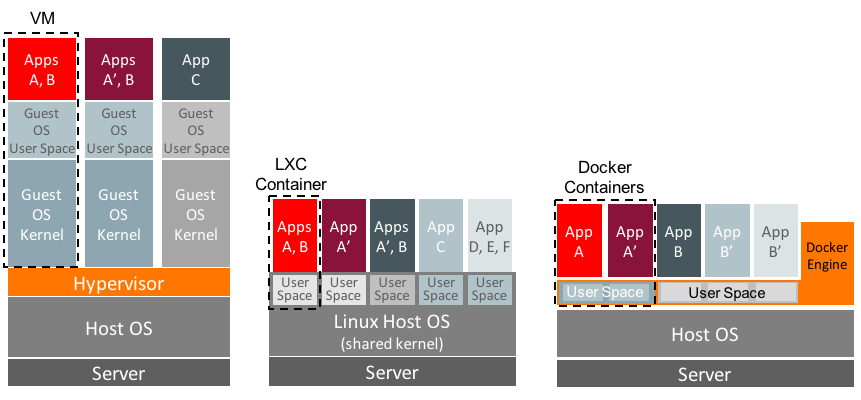
Architectural Differences
LXC/LXD containers are intended to run full Linux distributions, making them suitable for scenarios where a complete OS environment is needed. In contrast, Docker containers are designed to run individual applications and their dependencies, promoting a microservices approach. Docker's design philosophy emphasizes simplicity and ease of use, with a focus on creating, shipping, and running applications consistently across environments. For example, Docker is often used to package and distribute microservices, each running in its own container with minimal dependencies.
Resource Management and Performance
Both LXC/LXD and Docker offer efficient resource management, but their approaches differ. LXC/LXD's system containers can leverage the host's kernel and resources more effectively, resulting in lower overhead and higher performance. Docker, while also lightweight, may introduce additional layers of abstraction (such as the Docker daemon and container runtime), which can impact performance in certain scenarios. For instance, Docker's use of a layered filesystem can affect I/O performance compared to LXC's direct use of the host filesystem.
Ease of Use and Ecosystem
Docker is known for its user-friendly interface and extensive ecosystem. Docker Hub provides a vast repository of pre-built images, and Docker Compose simplifies multi-container deployments. These features make Docker accessible to developers and operators, promoting rapid adoption. LXC/LXD, while powerful, may have a steeper learning curve and a less mature ecosystem compared to Docker. However, LXD's client-server model and REST API offer robust management capabilities for advanced users.
Security Considerations
Both LXC/LXD and Docker provide isolation and security features, but their implementations differ. Docker uses containerd and runc for container runtime, which adds additional layers of security and isolation. LXC/LXD relies on Linux kernel features and apparmor profiles for isolation. While both approaches are secure, the choice between them may depend on specific security requirements and use cases. For example, LXC's direct use of kernel features may offer better performance, while Docker's additional runtime layers may provide more flexibility in certain environments.
Pros and Cons of Docker vs. LXC/LXD
Docker's primary advantage lies in its ecosystem, ease of use, and widespread adoption. It is ideal for developers looking to containerize applications quickly and deploy them across various environments. However, Docker's additional layers of abstraction may introduce resource overhead and complexity in large-scale deployments. On the other hand, LXC/LXD offers superior performance and resource efficiency, making it suitable for scenarios requiring high density and low overhead. Additionally, LXD's advanced management features provide greater flexibility and control for complex container environments.
Comparison with Virtual Machines
Resource Utilization and Overhead
Virtual machines (VMs) require a separate operating system instance for each VM, resulting in significant resource overhead. Each VM consumes CPU, memory, and storage resources, limiting the number of VMs that can run on a single host. In contrast, LXC containers share the host's kernel, reducing the need for redundant OS instances and minimizing resource consumption. This makes LXC containers more lightweight and efficient, allowing for higher density and better performance. For example, a single host might support dozens of LXC containers but only a few VMs due to resource constraints.
Performance Metrics
VMs have higher overhead due to the need to virtualize hardware and run separate OS instances. This can result in slower startup times and reduced performance compared to containers. LXC containers, sharing the host's kernel, start up quickly and perform efficiently, making them ideal for dynamic and high-performance environments. For instance, a development team can benefit from rapid container startup times, enabling faster testing and iteration cycles.
Isolation Mechanisms
VMs provide strong isolation by virtualizing the entire hardware stack, including the CPU, memory, and storage. This isolation is robust but comes with the cost of higher resource consumption. LXC containers provide isolation at the OS level using namespaces, cgroups, and chroot, which is sufficient for many use cases but may not match the level of isolation provided by VMs. For example, multi-tenant environments with strict isolation requirements might prefer VMs, while environments prioritizing performance and resource efficiency might opt for LXC containers.
Ideal Use Cases
VMs are suitable for scenarios requiring strong isolation, support for multiple operating systems, and compatibility with legacy applications. They are often used in environments where security and isolation are paramount, such as financial services and government sectors. LXC containers, with their lightweight nature and efficient resource utilization, are ideal for development, testing, and production environments that require high performance and scalability. For instance, cloud service providers can use LXC containers to offer scalable and cost-effective infrastructure services.
Pros and Cons of Using LXC/LXD
LXC and LXD offer several advantages, including lightweight and efficient resource usage, strong isolation and security, versatility for various use cases, and a strong community and support network. Their ability to run full Linux distributions in isolated containers makes them suitable for a wide range of scenarios, from development and testing to production deployments. LXD's advanced management features, such as profiles, snapshots, and network configurations, provide additional flexibility and control, making it easier to manage complex container environments.
Despite their benefits, LXC and LXD have some limitations. They may have a steeper learning curve compared to Docker, especially for users new to containerization. The ecosystem around LXC/LXD is less mature than Docker's, with fewer pre-built images and third-party tools available. Additionally, LXD's reliance on Linux kernel features may limit compatibility with non-Linux environments, making it less suitable for cross-platform deployments. For example, organizations heavily invested in Windows or macOS might face challenges adopting LXC/LXD.
Best Use Cases for LXC and LXD
Development and Testing Environments
LXC and LXD are ideal for creating isolated development environments. Developers can quickly spin up containers with specific configurations, test their applications in isolated environments, and easily revert to previous states using snapshots. This reduces the risk of configuration drift and ensures consistent development and testing environments. For instance, a development team can use LXD to create containers with different versions of dependencies, enabling thorough testing across various configurations.
Microservices and Cloud-Native Applications
The lightweight and efficient nature of LXC and LXD makes them well-suited for deploying microservices and cloud-native applications. Containers can be quickly scaled up or down based on demand, ensuring optimal resource usage and performance. LXD's advanced networking features enable complex network configurations, supporting microservices architectures with multiple interconnected services. For example, a cloud-native application can use LXC containers to deploy and manage individual microservices, ensuring high availability and scalability.
System Containers and Legacy Applications
LXC's ability to run full Linux distributions in isolated containers makes it suitable for running legacy applications that require specific OS environments. Organizations can use LXC to containerize legacy applications, enabling them to run on modern infrastructure without modification. This extends the lifespan of legacy applications and reduces the need for costly refactoring. For instance, a financial institution can use LXC to run legacy banking software in isolated containers, ensuring compatibility with existing infrastructure.
Hybrid and Multi-Cloud Deployments
LXC and LXD provide flexibility and portability, making them ideal for hybrid and multi-cloud deployments. Containers can be easily moved between different cloud environments, ensuring consistent performance and reducing vendor lock-in. LXD's client-server model and REST API enable centralized management of containers across multiple hosts and cloud providers. For example, an organization can use LXD to manage a hybrid cloud environment, deploying containers across on-premises and cloud infrastructure based on workload requirements.
LXC and LXD offer powerful solutions for containerization, providing lightweight and efficient environments for running full Linux distributions. Their strong isolation and security features, combined with advanced management capabilities, make them suitable for a wide range of scenarios, from development and testing to production deployments. While they may have a steeper learning curve compared to Docker, the benefits they offer in terms of performance, scalability, and flexibility make them valuable tools for modern infrastructure.


